
Articles, News, Research
Explore insights on identity, authentication, security, and cutting-edge technology shaping the future of Identity Access Management.
Featured posts
Security
19 Nov 24The Perils of Caching Keys in IAM: A Security Nightmare

Caching authentication keys can jeopardize your IAM security, creating stale permissions, replay attacks, and race conditions. Learn best practices for secure, real-time access control.
Ory Network
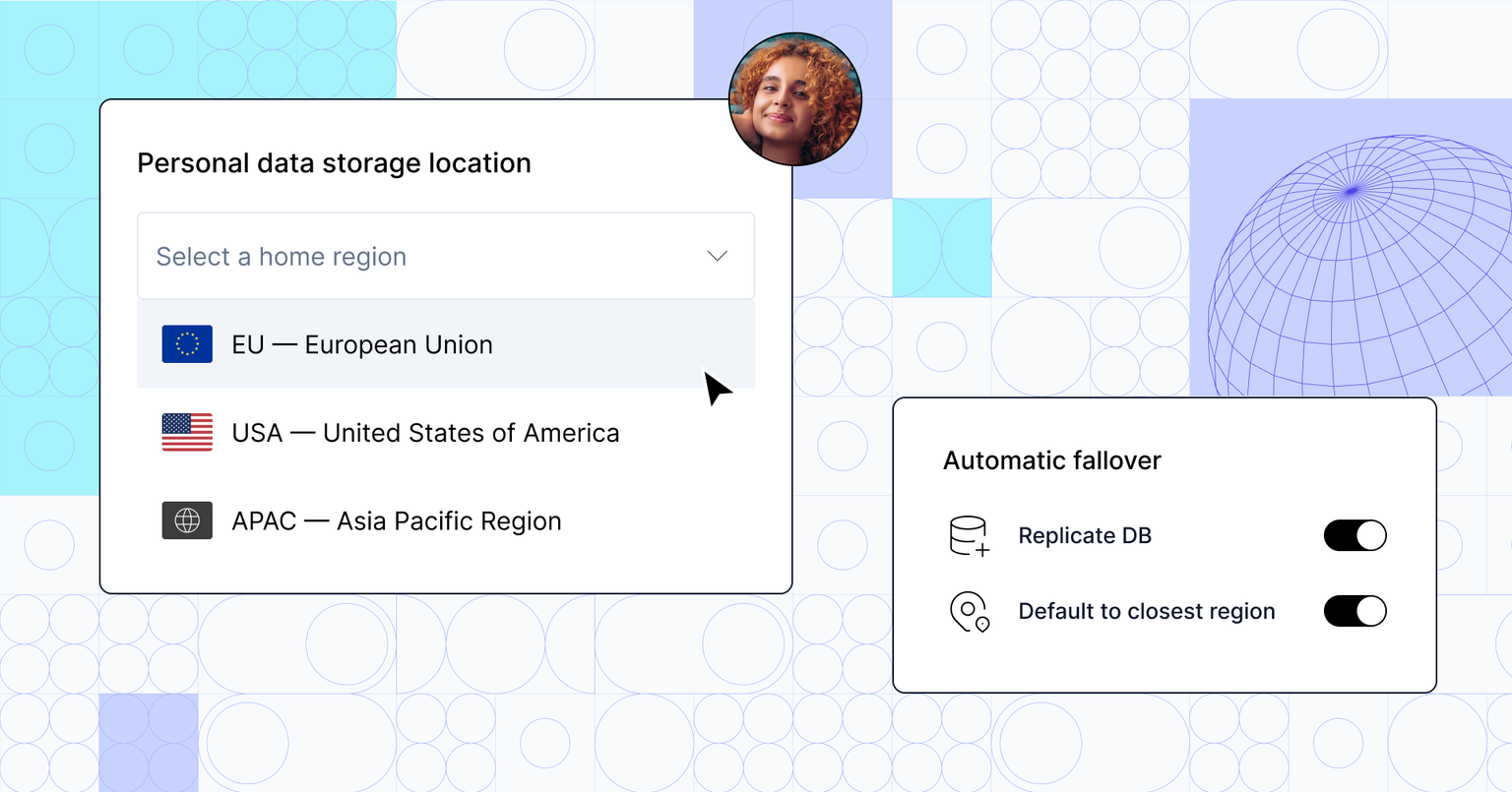
11 Jul 24Personal Data Storage with Ory Network

Learn how Ory solves data homing and data locality in a multi-region IAM network.

